Empowering Businesses with IT Solutions
Cyberattack Recovery: A Step-by-Step Guide
Read this comprehensive write-up, prepared by our professionals, on important steps to take soon after a cyberattack Recovery.
A Concise Overview of Cyberattacks
Many individuals, whether part of a technical team or not, usually know the basic definition of a cyberattack. Its concept revolves around the unauthorized access to various entities, such as computer systems, of a business.
These cybercriminals can either work independently or form a group to accomplish a goal. Now, stealing data is not the sole objective these threat actors have in mind. They might desire to change or destroy the information or even damage the entire system.
Therefore, many tech geniuses like us recommend their readers to opt for cybersecurity services, even if your company has not encountered any threat yet. This is because prevention is a lot more budget-friendly than looking for a solution after a cybercrime.
Furthermore, prior to proceeding with the steps, being knowledgeable about the forms of such attacks is wise as well. For your clarification, malware is an example.
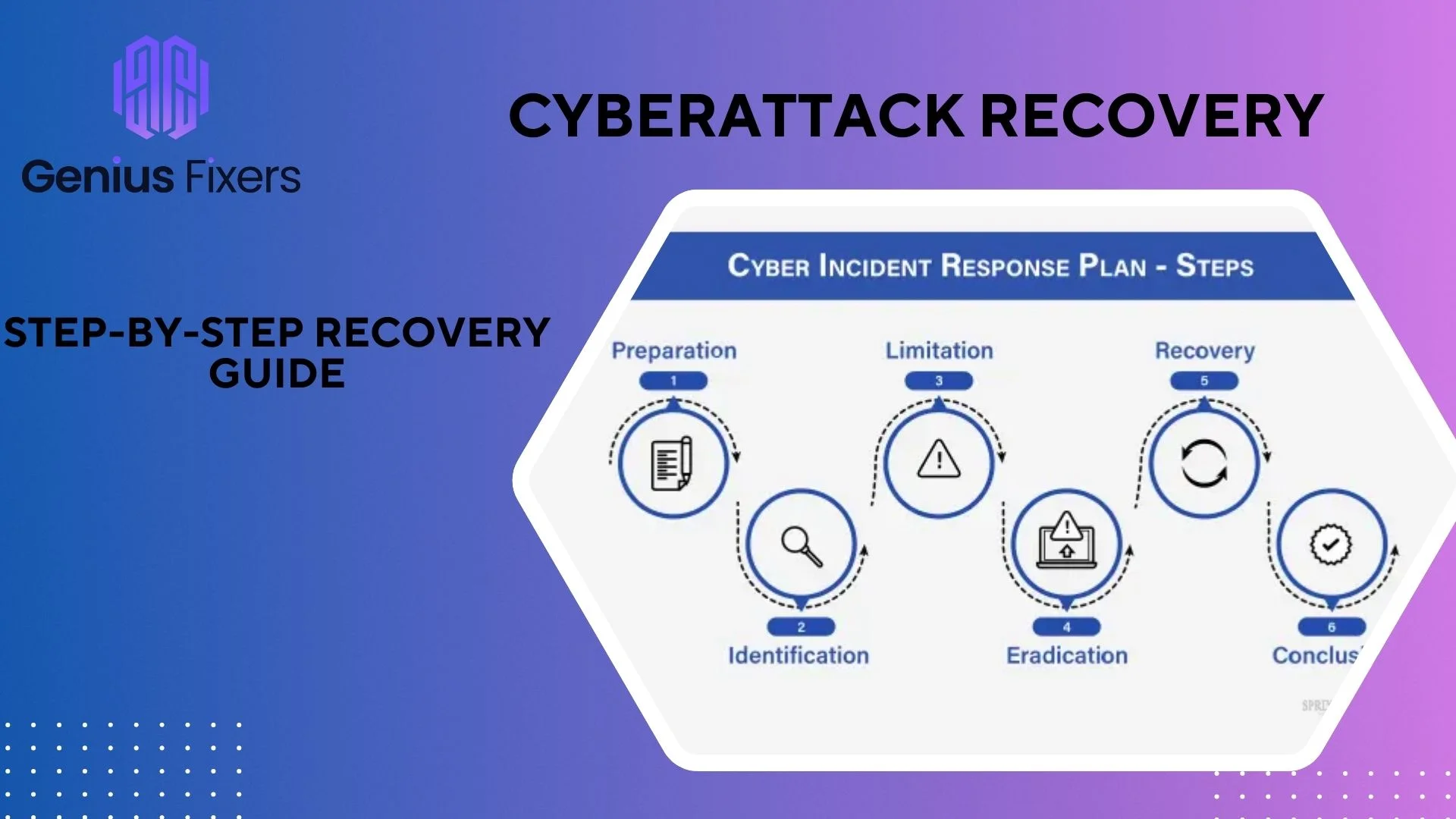
Recovering from a Cyberattack: The Vital Steps
Respond Quickly
First, you must take action as instantly as possible. For this purpose, you have to verify whether or not this is an actual attack. Most of the time, they are just false alarms that might waste your time and effort, something you must not opt for in a working environment.
Secondly, not letting it spread is your goal. Isolate the affected device or system. Ensure you have disconnected them from the internet. Next, you must value the proper firewall setting. Also, remember you have to keep everything as it is for the sake of evidence.
It is not merely about the evidence for legal matters. Basically, not removing any such information can assist you in near future analysis. This way, you will know more about your vulnerabilities. Hence, you can effortlessly work on preventive measures.
Determine the Damages
Moving ahead. The next task you must perform is focusing on the details. This is helpful in knowing the scope of the damage. For instance, take a look at your critical information. How much of it is still there, and which part has been stolen or altered?’
Moreover, this is a crucial step in determining what type of attack just occurred. This can further aid you in going in the right direction when looking for offerings from providers, such as phishing prevention training services.
Notify the Authorities & Individuals
There are a few authorities or people who are required to know immediately about such an unfortunate event. For instance, once you are familiar with its extent, you can talk to legal experts. They will instruct you about the possible lawful actions.
Another imperative step to take is to be brave and honest about what happened and explain it to the stakeholders. These are the ones affected the most by this serious situation. The examples encompass your staff, clients, and investors.
In terms of elaboration, you must let them know everything and satisfy these individuals. For the latter, you can enlighten them about your progress and what steps you are taking.
Threat Eradication & Recovering Lost Data
Until now, you might have already pondered on the necessary tasks to contain the threat. Then, there comes the complete destruction of it. You have to make the most apt attempts to prevent further violations. Modifying the passwords and applying security patches can work.
To recover your essential information, you have to rely on backups. Our BDR services are optimum in this matter. In fact, you must go for these services on a regular basis. Nonetheless, this step is only applicable if you have maintained a backup.
Rebuild Your Security Plan
It is time to revise your plan. The need for this change is because your former strategy did not work, leading to unfavorable circumstances. Make sure everyone’s responsibilities are clear in this document.
Besides, it must contain all the vital steps to deal with a severity like this. The reason behind creating such a plan is to assist the business in recovering as soon as possible and prevent the loss of more data.
Wrapping Up
The information we managed to put together today highlighted one of the significant aspects of the business and IT world. And this is what to do after a cyberattack. The latter is quite stressful due to the loss of data and money it provokes.
Nevertheless, contemplating the aforementioned steps can help you to a greater extent. For example, you must be quick in whatever you do, like disconnecting the infected devices from the internet. Also, you can comprehend the damages and contain the threat.
FAQs
What are the consequences of a cyberattack for a business?
There are diverse sorts of consequences that a business can face. Most of them are drastic. The common issues encompass data as well as financial loss. In many cases, they might also lose sensitive information related to their clients. This ultimately endangers the latter too.
What should I do soon after a cyberattack?
The appropriate way to handle such a situation is to take immediate action. You must already have an incident response plan prepared. If not, do it as instantly as possible by first amassing your relevant team members. Moreover, identify which devices or networks have been affected. Then, separate or isolate them or safeguard the other entities in your organization. If, for any reason, you are unable to handle this situation, consider our IT consulting services.
Whom should I talk to after such an incident?
You must figure out which individuals are the right ones, both internally and externally, who must have the knowledge of this situation. Your IT department and security team should typically know about this attack.
Afterward, there is the HR department in case your employees’ data has been lost.